Network Infrastructure
SWITCHING
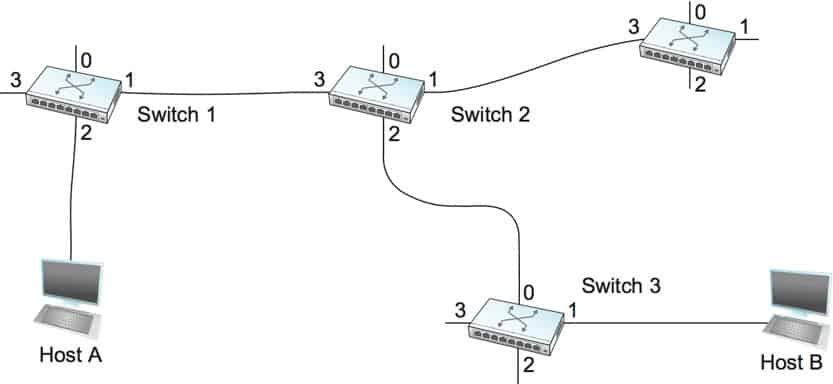
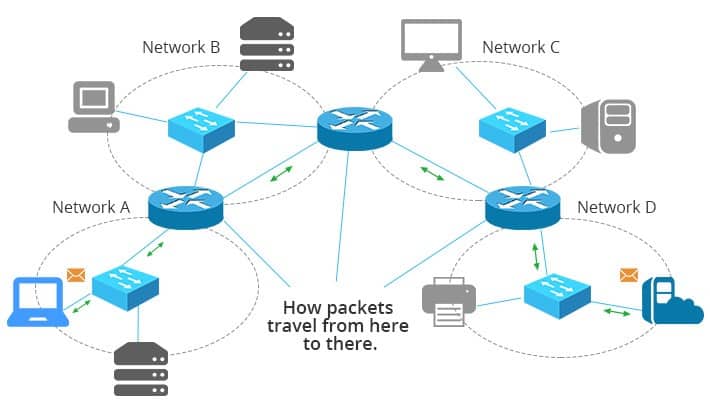
Switch Network switch or switching hub, bridging hub switch, What is a switch? Switch is a device in a computer network, just like a Hub serves to connect other devices together in the system. It uses packet switching, which receives, processes, and forwards data to the destination. Just one or more ports is not broadcast to all ports like a Hub.
Network switch play a large role in Ethernet local area networks (LANs). From medium to large systems, A LAN consists of a number of switches that manage the network, for example Small office/home office (SOHO) may use a single switch to a small office or residence which in the end may be used to connect to the router to use to connect to the internet or make Voice over IP (VoIP)
Packet Switching is a technology used for transmitting information by dividing data into multiple packets to make them smaller and then spread out through the network in different routes with different speeds because Packet Switching will find the proper path from the end to the destination for each packet if any packet goes wrong or can’t be forwarded. The system will immediately retransmit the packet. And when all the information has reached the recipient the destination computer will sequence data from received packets correctly.
Advantages
Disadvantages
The benefits of packet switching are: There is very little transmission error. Able to manage the problem of network traffic congestion. And can share the network with many users with low cost Packet Switching technology is currently being used in ATM machines and GPRS systems on mobile phones.
In implementing the switch in the network we can design it to suit our business applications. Switches are usually divided according to the application, which are small series, medium series, high series and highest series.
And in addition to bringing the right equipment to help design networking for small, medium, large businesses or businesses with multiple storefronts. At present, there is also the ability to manage the network through the cloud system, which makes it easy to manage. And easy to track work It also supports the use of IoT devices as well.
WIRELESS NETWORK
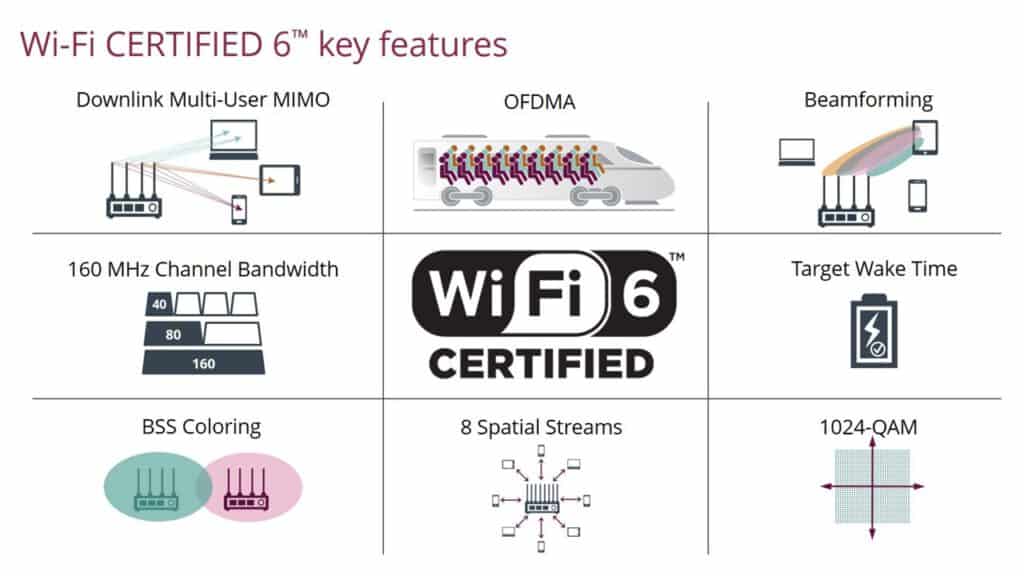
The hottest wireless technology right now is Wi-Fi 6, also known as 802.11ax. The focus is on connecting multiple devices to your wireless network at the same time, not comparing speeds. Next it is a management for the Client to get the speed that is suitable for use.


Institute of Electrical and Electronics Engineers (IEEE) and Wi-Fi Alliance They worked together to identify the scope of improvements to the current standard (802.11ac). The conclusion is a focus on performance under “typical” conditions to enhance the performance of the entire network holistically. It focuses on the highest advanced data rates under “perfect” conditions. A new standard called 802.11ax was released in early 2018 and was recently renamed Wi-Fi 6 by the Wi-Fi Alliance. Optimization of the way access points handle devices simultaneously. It’s no longer about comparing Wi-Fi speeds.
Institute of Electrical and Electronics Engineers (IEEE) and Wi-Fi Alliance They worked together to identify the scope of improvements to the current standard (802.11ac). The conclusion is a focus on performance under “typical” conditions to enhance the performance of the entire network holistically. It focuses on the highest advanced data rates under “perfect” conditions. A new standard called 802.11ax was released in early 2018 and was recently renamed Wi-Fi 6 by the Wi-Fi Alliance. Optimization of the way access points handle devices simultaneously. It’s no longer about comparing Wi-Fi speeds.
This latest standard is not only provide higher speed but it also enables new business services and use cases, including:
- IT/IoT Convergence and Smart Building Deployment.
- Real-Time application support for collaboration with video collaboration and Virtual Reality Secure Wi-Fi in enterprise and open networks.
What are the advantages / Advantages of Wi-Fi6 over Wi-Fi5, Wi-Fi4 that are commonly used at home? Why use Wi-Fi 6?
The value of using Wi-Fi6 compared to Wi-Fi5, Wi-Fi4
In using wireless enterprise level, it is recommended to use the wireless controller to manage the wireless system. What are the advantages of having a wireless controller that is superior to using a general Access Point?
Highlights of the Wireless Controller:
1. BANDWIDTH AP START DIFFERENCE
Bandwidth on Access Points is Total Wireless, unlike switches that are 100Mbps 1Gbps per port, so for enterprise wireless products, we will find that the starting point is about 867Mbps, 1.7Gbps and reaches 2.6Gbps, which is different from the consumer group that will see advertisements for 100Mbps, 300Mbps, some people may think that it’s already 300Mbps, but think about 100 people using 300Mbps, it will run only 3 Mbps per person because nowadays streaming is done together as life Content VDO that looks like it’s playing, whether on Facebook, Youtube, LINE, not including Snapchat and Instagram Stories groups.

2. WIRELESS A single name can be created
For the use in the consumer group that we see in the market, it will be found that 1 AP 1 name will walk anywhere, you have to stick to the name indefinitely. But for the enterprise group, that’s not. It can work through a wireless controller, making it the only name for Wi-Fi. Just like when we go to the mall, we are on the island of AIS, DTAC, True. Connected once walking across the country no need to go to a new connect for example. This will enable organizations to manage wireless more efficiently.
3. CLIENTLINK helps manage different devices
For real use we will find that the devices that come to the wireless connect have a variety of speeds. Whether the old 11a/g or the new 11n/ac, so without a good management system. will reduce the efficiency of work.

4. Eliminate interference problems
As wireless becomes popular, we find that there are many. Devices that use such signals as well, whether microware, Bluetooth headphones and even the Internet of Thing, all emit wireless signals. If there is no technology to help It will make the use of Wireless inefficient. This allows us to find the missing or not receiving the requested information. by dodging the signal on the channel that is not out.
5. Easy management via WEB MANAGE or MOBILE APP
If talking about the past We will find that we have to plug in the console. Must be proficient. Do that and do a lot. Today’s work is easier. Just plug the POE into the Access Point, we will find that access point on our computer and start Setting. You can access settings on either computer, iPad or even mobile app.
6. NEW ERA VIRTUAL WIRELESS CONTROLLER
Everything is virtual these days, wireless as well. Newer Access Point devices will find that there is no separate Wireless Controller box because the Access Point can act as a master or controller.
7. High performance security system
Wireless networking with built-in security, security functions include connecting to an authentication system, assigning and controlling user access rights to the wireless network, end-to-end encryption. State-aware firewall , There is a spectrum analysis system and protection against threats on wireless networks (Wireless IPS), etc.

NEXT GENERATION FIREWALL
Next Generation Firewall (NGFW) It is a highly effective firewall. and able to deal with complex threats by various functions Added is different from the general Firewall is that the application layer access can separate the use of the application Layer from using the LINE program, Facebook, YouTube or what type of program Makes it possible to set policies to control the use of those applications, for example within the organization setting the right not to use YouTube during working hours, etc. also have:
- IPS (Intrusion Protection System) Intrusion detection and response system when it detects information of a nature that poses a risk to the network It will prevent that information from entering the network.
- Antivirus To enhance the effectiveness of protection against common viruses such as Malware, Trojan, Spy Ware, etc., that will enter the network to damage data or computer systems.
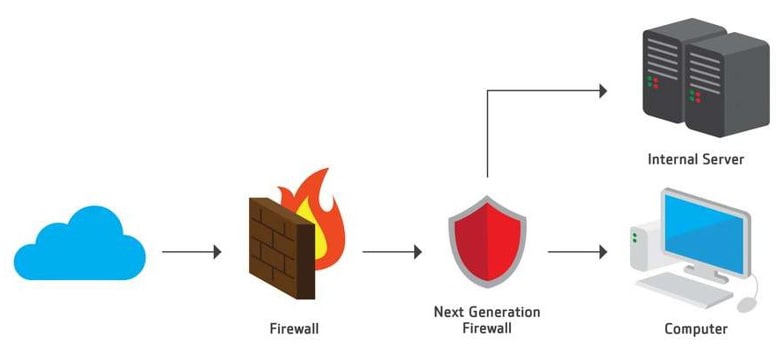
- Network security equipment (Firewall) is a need for more advanced network technology (Next Gen Firewall).
- Get more traffic (High Performance)
- Including durability in service (High Availability)
In addition, there must be a network security reporting system. for administrators and administrators get the right information Helping to analyze the work efficiency. Therefore, there must be an excellent network security system (Firewall) for effective information security as well as being able to provide computer networking services safely and with maximum efficiency.
Next generation firewall secure your network and more ability
SD WAN
(Software-Defined Wire-Area-Network)
Software-Defined Wide-Area Network (SD-WAN) It is a technology that connects the head office and branch offices that are scattered whether in or out of the country. With the strengths that increase the efficiency of connecting applications equal to that of MPLS connections at many times cheaper. It’s still stable. secure and easy to manage from the center As a result, many organizations around the world are starting to pay more attention to SD-WAN technology.
For organizations that are already connected between branches with MPLS or other connections, having a redundant link to be prepared for when the primary link fails or crashes can improve business continuity, but the MPLS investment is. Alternate links can be exorbitant. Plus, it doesn’t help benefit when the main link is still usable. SD-WAN is cheaper to help meet this point. By dividing the traffic of enterprise-critical business applications run on MPLS, while general traffic runs on SD-WAN instead, reducing the burden on the primary link. and make the most of the backup link at the same time.
Gartner defines four features of SD-WAN:
- Must support multiple connections such as MPLS, LTE, Internet, etc.
- Dynamic path selection, such as load sharing across the WAN
- Has a very easy to use interface, supports Zero-touch Provision, can be used as easily as a home Wi-Fi.
- Support for VPN or third-party services such as Wan Optimization Controller, Firewall, Web Gateway, etc.
SD-WAN (Software-Defined Wide-Area Network)
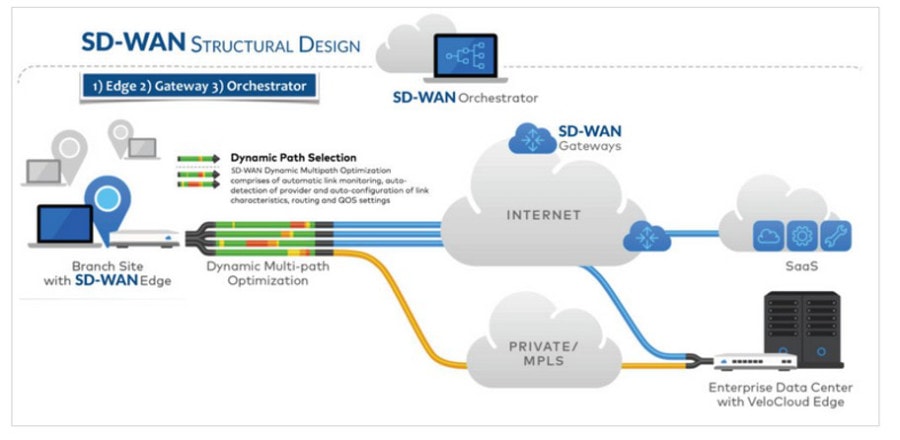
Solving the grievances of the SD-WAN:
1. Does SD-WAN require hardware to be purchased as well? Or is it just the software as its name suggests?
- It is hardware managed by specific software that runs in the device.
2. Abbreviations such as MPLS should be noted what they are. Readers may not be 100% technical.
- MPLS is a label-based Switching that can be used for multiple protocols, it’s similar to a local translation. But just literal translation probably doesn’t define the word MPLS. Generally, an MPLS provider is a Provider. A Provider router that provides MPLS services is called a PE (Provider Edge) or a router that is connected to a customer. As for the router that is in the core, we can’t continue. To disappear further MPLS cannot be used at that point because MPLS can only be used at the PE point. Which one is the direction of the input data is called Ingress Router and the output data is Egress Router.
3. SD-WAN Edge, SD-WAN Orchestrator is Hardware or Software? It’s not said.
- SD-WAN Edge: Refers to SD-WAN at the destination address, e.g. by branch in each region.
- SD-WAN Orchestrator: The design manages all SD-WAN from a central location. This makes it easy to maintain SW/HW.
Network Management
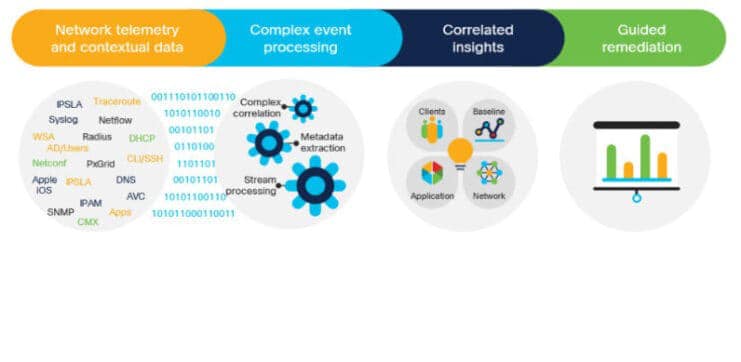
Network Management Act as the control center and watch the network have a warning system when any part of the network is malfunctioning or crashes Let administrators know immediately and go in to make corrections quickly. The main function of the NMS is to monitor the network at all times. Make a report on network usage statistics. For example, statistics of traffic, user volume, can be graphed for system administrators to analyze and plan network expansion. Administrators can also monitor and modify the system from a central point. Including software installation system configuration for distant network devices NMS is a large network device. Or a public network service provider with a large number of subscribers is required. Because it is a device that makes monitoring the system more efficient. Nowadays, even the Intranet has various devices. As the combination becomes more complex, NMS plays an important role in the administration and management of Intranet networks.
Network Management It is the process of maintaining and managing computer networks. Services provided in accordance with this regulation include fault analysis, performance management, network provisioning, and service quality maintenance. Software that allows network administrators to perform their functions is called network management software network management also discovers network devices and creates a network topology map. The network view is created this way and whenever you click a network device in this map you will be able to access the selected device. You can configure, manage and operate this device.
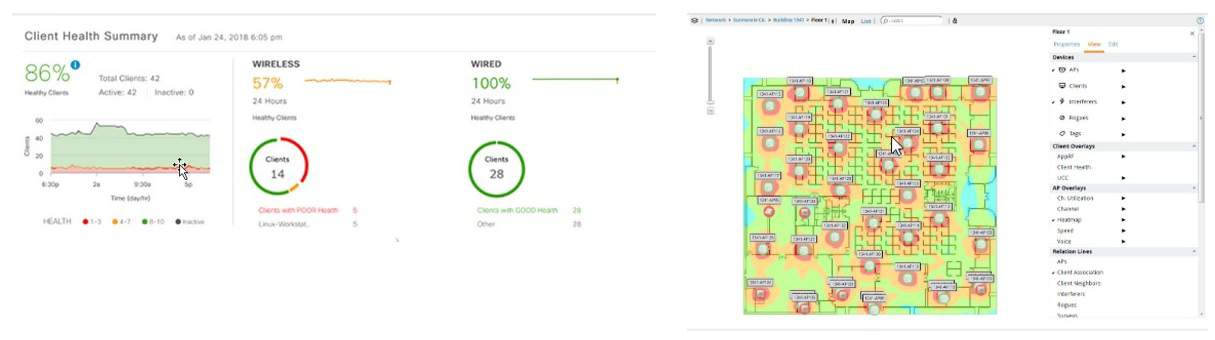
AI and Machine Learning, combined with additional resources, proactively optimize your network and provide a better user experience.
Network Management Benefits :
- Save time: Noise and false positives are minimized while the issues that have the greatest impact on your network are correctly identified.
- Reduce workload: AI-powered technology can proactively find the root cause of your biggest network problems quickly.
- Fast Troubleshooting: Machine learning algorithms, automatic correction options for quick troubleshooting
- Helping you excel: Your network’s performance increases while you spend less time running and troubleshooting.
SSL VPN (Secure Socket Layer Victual Private Network)
SSL VPN (Secure Sockets Layer + Virtual Private Network)
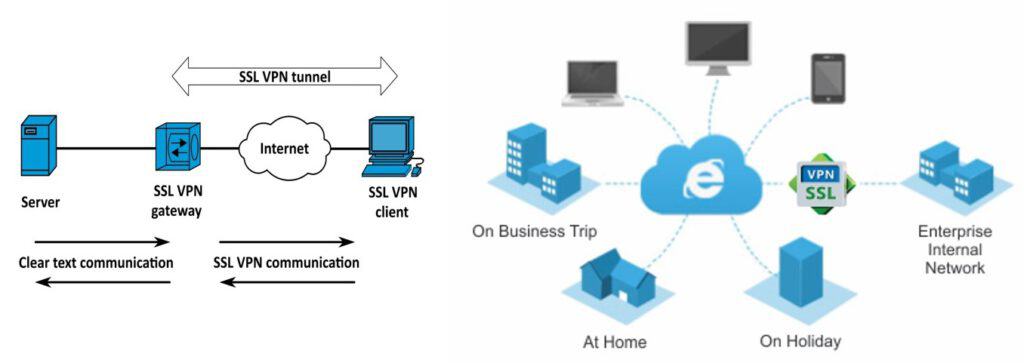
It is a feature of providing networking services only within the organization that can be used. By using public networks or the Internet as a medium for transmitting information between departments within the organization By using data encryption to create a virtual network. So that the information transmitted together remains secure. And still maintain the confidentiality of the information as if it was sent within the organization.
SSL VPN is a type of virtual private network (VPN) that uses the Secure Sockets Layer (SSL) protocol, or often its successor, the Transport Layer Security (TLS) protocol in standard web browsers to provide security. Ability to access VPN remotely SSL VPN allows any Internet-connected device to establish a secure remote access VPN connection with a web browser. SSL VPN connections use end-to-end (E2EE) encryption to protect data transmitted between Endpoint client software with SSL VPN server through which clients connect securely to the Internet.
SSL VPN There are appliance box, Virtual Machine and could service both as SSL VPN only and feature on Next gen firewall.
SSL VPN Client Can download dynamically allows users to access the network and connect to enterprise applications. There is a helper that is easy to use. which makes deployment easier. And a powerful tool to monitor and manage sessions in real time is a single device VPN, security and routing solution.
In addition, we can bring Multi Factor Authentication to increase the security for users to use VPN in the corporate network.