Security System
Log & Next-Gen SIEM
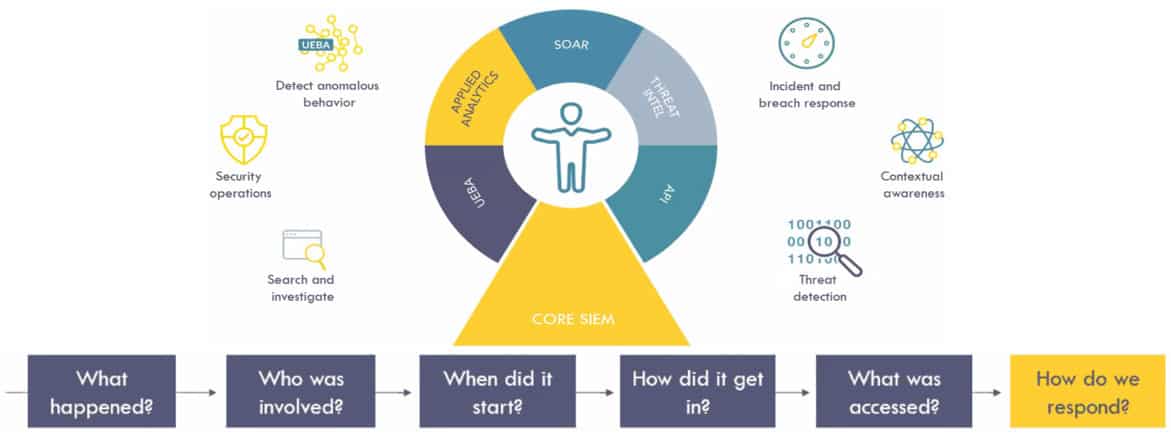
Security information and event management (SIEM)
The function of SIEM is log storage and collection of various equipment. To take advantage of information from various sources. It will analyze the situation quickly and efficiently. All data will be able to correlate to find the source and purpose in various forms. It also knows how to track threats or detect incoming threats and can used rule to notify administrators.
Features & Benefits

If you are looking for System Log Management or Next-Gen SIEM and Log to keep to the standards Computer Act or PDPA.
Network Access Control
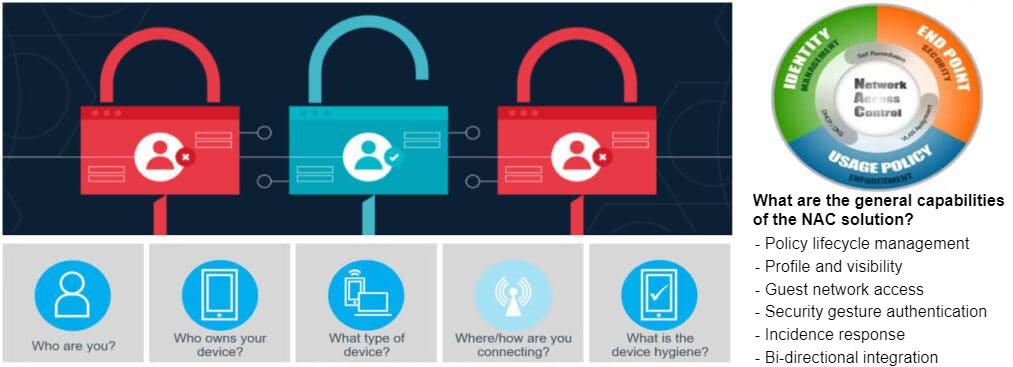
Network Access Control The control permission to access the network (Network Access Control), in which we can control access to the network. Initially, the NAC device itself must recognize and recognize other devices. in our network before It verifies and classifies all devices in the network and then performs authentication to assign permissions to all devices in the corporate network. It can also detect and stop attacks that occur automatically, such as scanning in the network within the organization or trying to access abnormal ports within the organization or sending abnormal emails, etc. Reports can also be customized to collect information and investigate security issues to meet the requirements or compliance requirements of the organization.
Features & Benefits

How Network Access Control can help the organization?
Endpoint Security

Endpoint Security It is a real-time security and virus removal solution from central to endpoint, capable of eliminating various threats. comprehensively and can be managed centrally to the terminal by setting policy settings centrally to the terminal for security. In management, it also helps to close the vulnerabilities of threats that will enter the organization. It also reduces management costs and increases efficiency in the organization. It can also analyze information that looks like a virus. or suspect after the analysis, it will respond to detect abnormalities and will manipulate the data according to the action set to avoid too much damage.
Features & Benefits

How good is Endpoint Security?
Gateway Security

Secure Mail Gateway
Filters all incoming and outgoing emails to protect your organization from known and unknown threats. This includes spam, phishing and all types of malicious attachments that come with emails and data leaks. It makes it easy to manage, saving time in daily email security work. It also increases the efficiency of the user’s work.
Features & Benefits
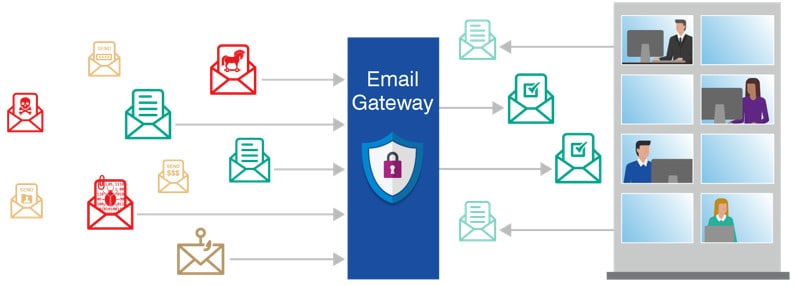
Secure Mail Gateway Why is it necessary?
Secure Web Gateway
Enforce a secure Internet use through flexible policy management and sensitive in receiving – sending information on the website and platforms. It also prevents unintentional data leaks into websites by scanning or detecting content in real time for prevent intrusion and prevent the upload of risky documents to different websites or platforms. It also monitors web traffic and prevents inappropriate website traffic or malicious or suspicious web or files indicating malicious content. considered a good protection for sensitive data both in and out of the organization and makes it possible to use the website safely for users.

Features & Benefits

How important is Secure Web Gateway?
Secure Internet Gateway
The ability to protect against various threats on the Internet for users. which can be checked analyze and limit access. It also protects and analyzes suspicious files and considered an answer for organizations that have a need for security.
Features & Benefits
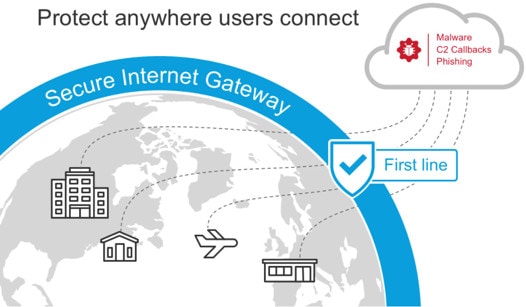
Secure Internet Gateway จำเป็นต่อการใช้งานอย่างไร?
Multi Factor Authentication

Multi Factor Authentication
The authentication requires users to specify up to two-factor authentication. In order to verify the identity of users to authenticate before they enter the system. It is considered a modern access and More efficient for organizations that need security.

Features & Benefits
Multi Factor Authentication What help?
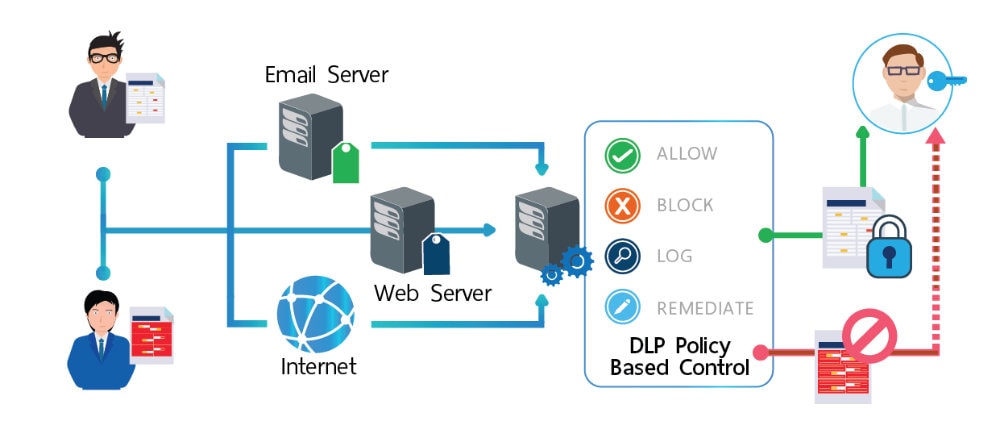
DLP
DLP Detect and prevent leaks of sensitive corporate data and In order not to lose data or files and also protect files with important content such as start by sorting out the types of data or prioritizing first. After that, various data groups will be analyzed by setting a policy to prevent data leakage of each type of information from various channels of use. with notification to the administrator of the organization. If important information is passed out